Home » #Memoir

Rubik’s Cube Challenge: Motivation and Creativity at PeopleStrong workplace Year 2012
Corporate, corporate-organizations, Gurgaon, Haryana, Motivation, PeopleStrong, PeopleStrong HR Tech, Year2012In December 2012, I found an innovative way to break the monotony of office life and boost my team’s creativity at PeopleStrong HR Tech, sector 34 gurgaon office. As a leader, I firmly believe that regular motivation at workplace is crucial for employee retention—far more impactful than monetary rewards or occasional outings. To inspire creativity,…
For startups, attracting funding is essential for scaling operations and driving innovation. Building on my 18+ years of expertise in the tech corporate field, I specialize in delivering cutting-edge, scalable solutions and leading teams toward operational success. I emphasize that financial statements, particularly the balance sheet, are critical for investors to evaluate a business’s health,…
Running a startup often feels like juggling multiple tasks while navigating uncharted waters. Amidst this in finance, the balance sheet stands as a vital compass, helping founders make informed financial decisions. For a startup, financial health is as important as the product or codebase itself. This startup finance concept, will provide a step-by-step guide on…

Moments from Graduation Day: Reliving the 4th Convocation of NIT Rourkela (2006)
Graduation day is a milestone etched in memory, and the 4th Convocation at NIT Rourkela on 16 December 2006 was no different for me. This moment marked the culmination of years of hard work, camaraderie, and the shared dreams of a small-town boy venturing into the world. As I stood among my peers, holding the degree that…

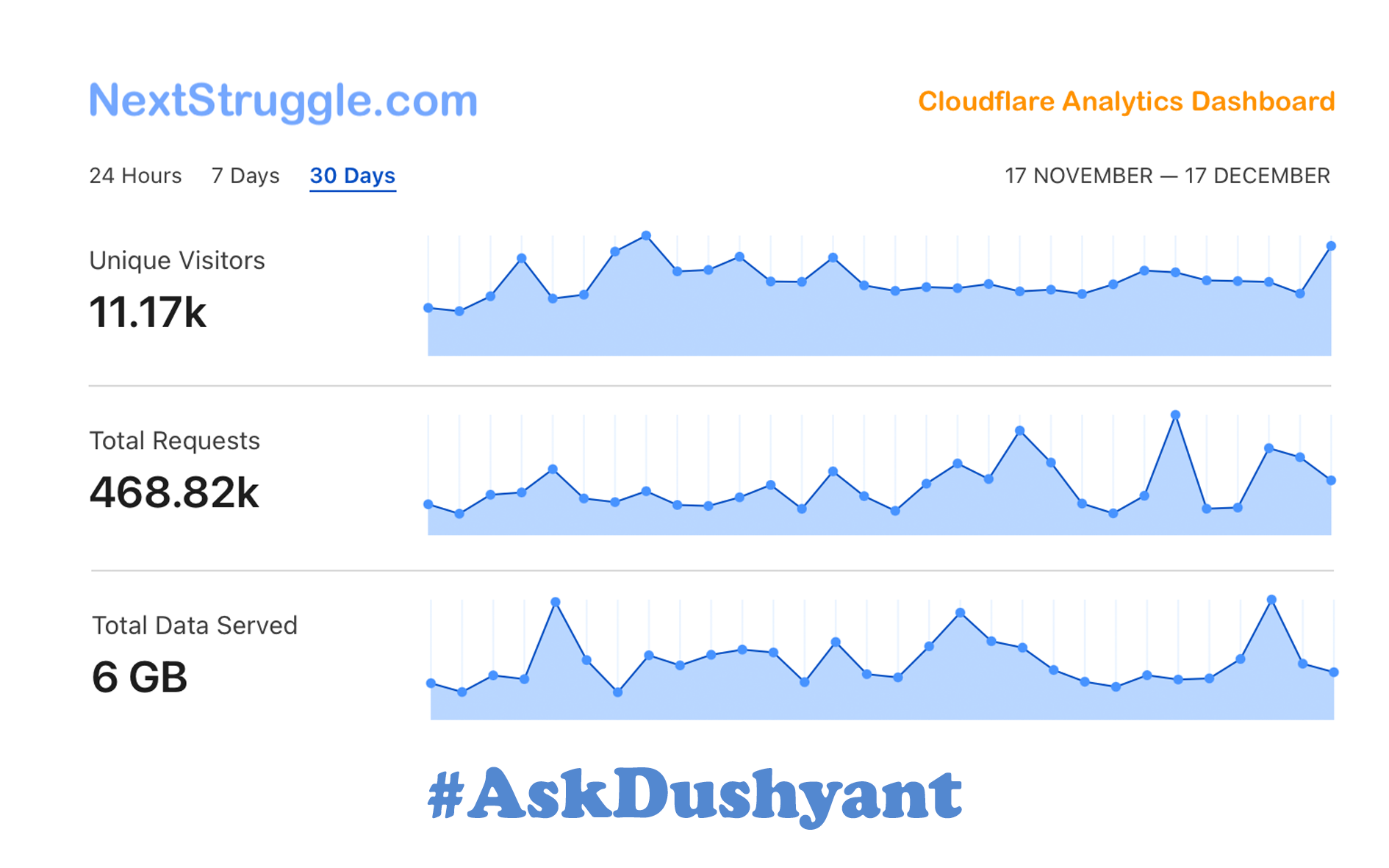
The Journey of #AskDushyant: How I Built NextStruggle and Created My Digital Identity
A year ago, I embarked on a journey to build my personal tech platform, NextStruggle, and carve out a unique digital identity as #AskDushyant. At the start, I had little idea of what to write. I began with posts on current issues and snippets of notable tech information. However, as I dive deeper, I realized I possessed…

Immersing in Bengali Traditions: My Navratri festive moments in CR Park, 2012
Navratri has always been a profound period of reflection and spirituality for me, where simplicity in thought, diet, and behavior becomes a way of life. In 2012, I had the chance to immerse myself in the grandeur of Navratri celebrations at Delhi’s CR Park (ChitRanjan park), a vibrant hub of the Bengali community known for…

Bengali Durga Puja and Navratri in CR Park: A Memoir of Spiritual Festivities Year 2012
Navratri 2012 was a spiritual and cultural revelation for me, as I immersed myself in the grandeur of Durga Puja celebrations at CR Park in Delhi. The vibrant pandals, adorned with intricate depictions of Goddess Durga, captured the essence of Bengali traditions and showcased India’s incredible cultural diversity. Each evening brought a new experience—whether it…

Khajuraho Chronicles: A 2013 Biking Odyssey Through History and Heritage
In 2013, I embarked on a memorable biking adventure along with Alok Gautam (NIT Rourkela Colleague) to Khajuraho, reliving India’s historical richness and cultural vibrancy along the way. Khajuraho, with its intricate temples and profound artistry, crowned the experience, blending spiritual energy with human creativity on stones. The journey to Khajuraho wasn’t just a sightseeing…

From Gurgaon to Nainital: A Ride Through Friendship and Adventure Year 2011
In 2011, I embarked on yet another week-long bike adventure, a ritual I had maintained for three years. This time, the destination was the serene hills of Nainital, Uttarakhand. Having recently joined PeopleStrong, I found a travel partner in Anurag Sinha, a colleague eager to experience his first long-distance ride. With my Bajaj Avenger packed…

Two Bikes, One Road: My 2011 Ride to Nainital’s Scenic Bliss
In 2011, I embarked on a bike ride to Nainital, a trip that marked the beginning of my unforgettable adventures in the hills. Riding my trusty Bajaj Avenger alongside my friend Anurag Sinha on his Pulsar, we journeyed from Gurgaon through scenic stops like Garhmukteshwar and Bhimtal. The road tested our endurance while gifting us…

Riding Back from Nepal: A Biker’s Tale of Adventure and Friendship Year 2011
BikeRide, Moradabad, MotorcycleDiary, Nepal, OpenRoad, Rudrapur, Uttar Pradesh, Uttarakhand, Year2011In 2011, my solo bike journey on my trusted Bajaj Avenger to Nepal during my Nainital ride remains one of my most cherished memories. Crossing the border into Nepal was a personal milestone, filling me with an indescribable sense of accomplishment. As I documented my final moments in Nepal, taking in the last frames of…

Riding Back from Nepal: Memories, Milestones, and Friendship Year 2011
BikeRide, Moradabad, MotorcycleDiary, Nepal, OpenRoad, Rudrapur, Uttar Pradesh, Uttarakhand, Year2011My Nepal trip in 2011, during a bike ride from Nainital, remains one of the most cherished adventures of my life. Riding my trusted Bajaj Avenger, I crossed the Indian border solo to Nepal, an achievement I had long dreamed of. I captured the riding back from Nepal to India towards Rudrapur, where i witnessed…

Revisiting Newton: A Journey Through My Father’s Hometown Year 2009
In 2009, during my soul-searching bike trip, I had the privilege of revisiting Newton, my father’s hometown, known for its historic coal mines. This English-named town owes its title to an English surveyor, Newton, who worked there during the British colonial coal mining era. My grandparents spent their lives working in these coal mines, and…

Newton Through my lens: Memories of My Father’s Coal Mine Town in 2009
During my 2009 soul-searching bike trip, I revisited Newton, my father’s coal mining hometown, a place steeped in history and personal connections. Newton, named after an English surveyor, was once a bustling coal town where my grandparents worked and my father spent his formative years. I relived childhood memories as I attended a family relative…

Crossing Borders: Adventurous from India to Nepal on Two Wheels Year 2011
The spark of my biking passion was ignited during my childhood when I watched a Discovery documentary about Harley Davidson. That vision of freedom on two wheels stayed with me, leading to a lifelong dream of owning a cruiser bike and exploring India’s diverse landscapes. My Bajaj Avenger became my trusted companion for these escapades.…

Crossing Borders and Boundaries on two wheels: Memories from Nepal Year 2011
In 2011, A spontaneous adventure to Nepal make my dream of crossing borders on a bike came true. During my Nainital ride with friend Anurag, after reaching Nanital, I decided to further continue on my Bajaj Avenger towards Nepal, reaching Tanakpur and then crossing the Indian border at Gadda Chowki into Mahendra Nagar, Nepal. Riding…

Experiencing the Kavad Yatra: Devotion and Community Spirit in Delhi NCR Year 2012
Life in Delhi NCR has gifted me some of the most enriching experiences, blending cultural diversity with profound spiritual traditions. Among these, the Kavad Yatra during the holy month of Sawan as per hindu believes, holds a special place. Growing up, I saw glimpses of this sacred journey in TV serials and songs, but witnessing…

A Journey of Faith: Capturing Kavad Yatra in Delhi NCR Year 2012
My cherished memories of Year 2012 is experiencing the vibrant Kavad Yatra in Delhi NCR during the auspicious Sawan month. Witnessing this spiritual journey firsthand, I was deeply moved by the selfless dedication of local communities who set up pandals to offer food, shelter, and support to Shiva devotees, or “Bholas,” on their sacred pilgrimage…
Like many, when you start earning, the desire to grow wealth often leads to the stock market—a place where everyone dreams of getting rich with basic knowledge. However, understanding the fundamental rules is crucial before diving in. It took me years to grasp these basics. Are you curious about the stock market but intimidated by…
Equity investing has become a cornerstone of personal finance for individuals looking to grow their wealth. With nearly two decades in the tech corporate world, building innovative tech solutions, I too was drawn to the allure of the stock market. Drawing from my experiences, this concept offers a comprehensive guide to equity investing. From understanding…