Home » #Technology
Real-time data streaming is transforming how businesses process and analyze information. With technologies like Apache Kafka, Hadoop, and NoSQL databases, you can build powerful, scalable systems to handle real-time data streams. With 20 years of experience driving tech excellence, I’ve redefined what’s possible for organizations, unlocking innovation and building solutions that scale effortlessly. My guidance…
Web crawling frameworks have revolutionized how we collect data from websites, making the process faster and more efficient. However, choosing the right framework depends on your specific needs, including website complexity, data format, and interactivity. For over two decades, I’ve been igniting change and delivering scalable tech solutions that elevate organizations to new heights. My…
Data is the new oil, and in today’s tech world, businesses are swimming in oceans of structured, semi-structured, and unstructured data. With 20 years of experience driving tech excellence, I’ve redefined what’s possible for organizations, unlocking innovation and building solutions that scale effortlessly. My guidance empowers businesses to embrace transformation and achieve lasting success. Traditional…
Processing large datasets efficiently with Hadoop is a common task in data-driven industries. With the mrjob library in Python, you can write and run MapReduce jobs on Hadoop clusters or locally. The best part? You can access data stored in various storage systems like local file systems, AWS S3, Google Cloud Storage, and HDFS. For over two…
QR codes have rapidly evolved from a functional tool into a branding powerhouse. By customizing QR codes with logos, colors, and shapes, you can create a distinctive brand identity while enhancing customer engagement. Two decades in the tech world have seen me spearhead groundbreaking innovations, engineer scalable solutions, and lead organizations to dominate the tech…
In this tech concept, we delve into how Hadoop tackles processing datasets that traditional methods of storage and processing simply cannot handle, showcasing its groundbreaking approach to data challenges. Original Tech Concept: Hadoop and NoSQL: Breaking the Shackles of Traditional Databases>> When dealing with massive datasets, like log files or large text collections, extracting actionable…
Web crawling and parsing are transformative techniques that unlock the power of the web, enabling us to collect and interpret vast amounts of data. These methods serve as the foundation for everything from search engines to cutting-edge, data-driven tools, innovative tech solution. With over two decades in the tech world, I had drove innovation, engineered…
Web crawling and parsing are transformative techniques that unlock the power of the web, enabling us to collect and interpret vast amounts of data. These methods serve as the foundation for everything from search engines to cutting-edge, data-driven tools, shaping how we extract value from the digital world. With over two decades in the tech…
Web crawling and parsing are powerful tools that drive innovation and efficiency across various industries. By automating data collection and analysis, they unlock endless possibilities for businesses and developers alike. With two decades in the tech world, I have spearhead groundbreaking innovations, engineer scalable solutions, and lead organisations to dominate the tech landscape. When businesses…
In today’s fast-paced digital age, vast amounts of data are generated every second. Web crawling and parsing are two powerful techniques that enable us to collect and make sense of this data. From search engines to data-driven tools, these processes form the backbone of how we interact with and extract value from the web. Over…
Imagine scanning a QR code only to find it no longer works—was this intentional or a security lapse? QR code expiration ensures that QR codes serve their purpose within a limited timeframe, protecting users and enhancing operational efficiency. With nearly two decades of experience in the tech corporate industry, I have spearheaded initiatives that drive…
QR codes are everywhere today. From marketing campaigns to payment systems, these versatile tools make it easy to connect the physical and digital worlds. With nearly two decades in the tech corporate industry, I have led initiatives that drive innovation, build scalable solutions, and guided tech teams to success. Extending this expertise to my branding…
For startups, attracting funding is essential for scaling operations and driving innovation. Building on my 18+ years of expertise in the tech corporate field, I specialize in delivering cutting-edge, scalable solutions and leading teams toward operational success. I emphasize that financial statements, particularly the balance sheet, are critical for investors to evaluate a business’s health,…
Running a startup often feels like juggling multiple tasks while navigating uncharted waters. Amidst this in finance, the balance sheet stands as a vital compass, helping founders make informed financial decisions. For a startup, financial health is as important as the product or codebase itself. This startup finance concept, will provide a step-by-step guide on…

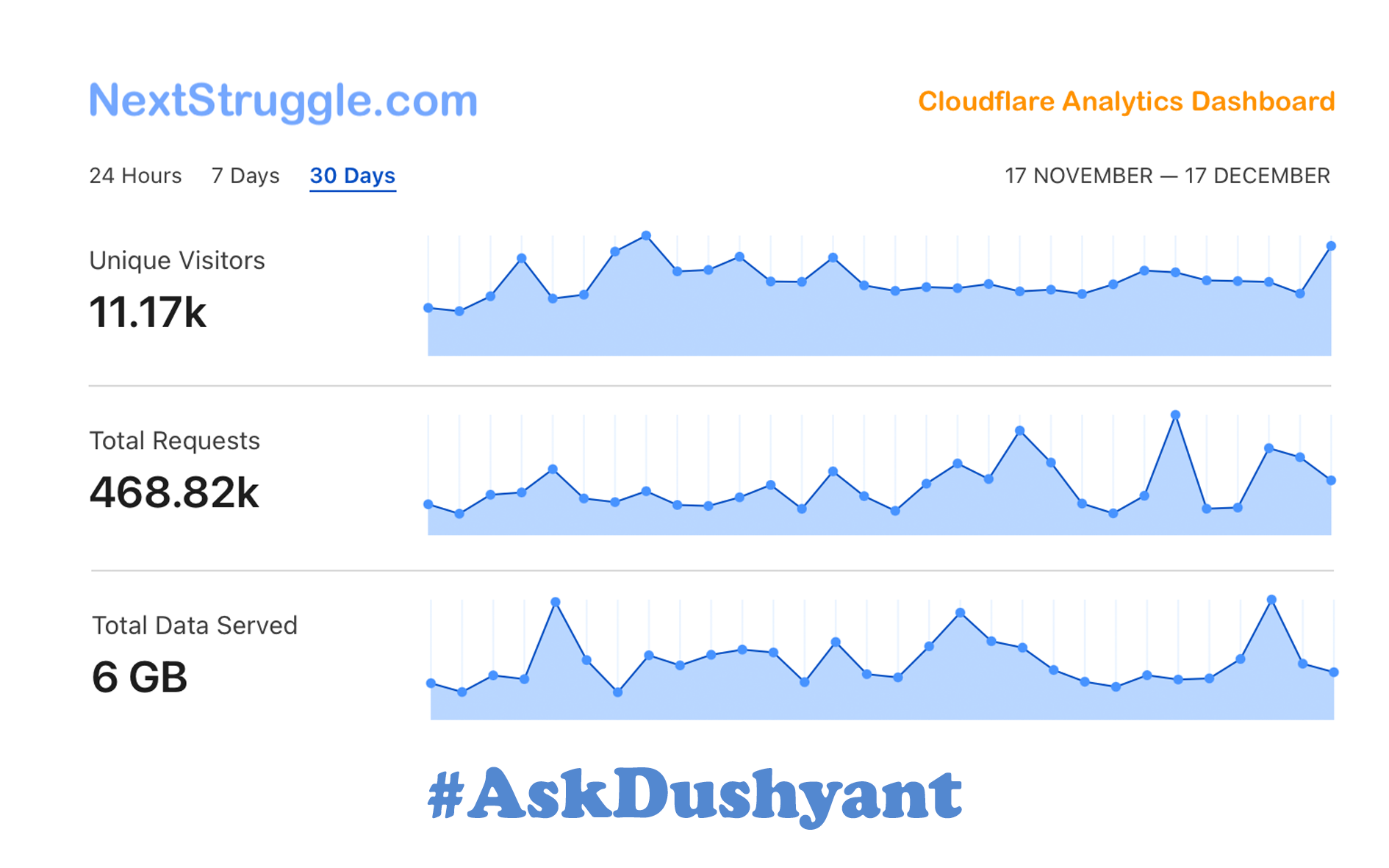
The Journey of #AskDushyant: How I Built NextStruggle and Created My Digital Identity
A year ago, I embarked on a journey to build my personal tech platform, NextStruggle, and carve out a unique digital identity as #AskDushyant. At the start, I had little idea of what to write. I began with posts on current issues and snippets of notable tech information. However, as I dive deeper, I realized I possessed…
Like many, when you start earning, the desire to grow wealth often leads to the stock market—a place where everyone dreams of getting rich with basic knowledge. However, understanding the fundamental rules is crucial before diving in. It took me years to grasp these basics. Are you curious about the stock market but intimidated by…
Equity investing has become a cornerstone of personal finance for individuals looking to grow their wealth. With nearly two decades in the tech corporate world, building innovative tech solutions, I too was drawn to the allure of the stock market. Drawing from my experiences, this concept offers a comprehensive guide to equity investing. From understanding…
Equity forms the backbone of any startup. Understanding key equity terms empowers founders to navigate funding, protect ownership, and build sustainable growth strategies. Leverage my 18+ years of experience in the startup tech domain, crafting scalable solutions and driving technology innovation. Keeping key startup concepts at hand is crucial in navigating corporate nuances. This startup concept…
When seeking early-stage funding, startups often choose between SAFE (Simple Agreement for Future Equity) and Convertible Notes. Both instruments provide flexibility for startups and investors, but they differ in structure, terms, and their impact on equity. Backed by 18 years of experience in the startup tech corporate sector, I’ve specialized in delivering scalable, future-ready solutions and building high-performing…